In windows, every service has its process (exe file). Every process is running under the service privileges.
We can exploit this fact in several cases. we will focus on 2 of them:
- the process path has no quotes, there is a folder with space in its name and weak permission are set on this folder.
- non admin users has MODIFY permissions on the exe file.
In both cases we have to make sure that the service is running under “system” and that it is automatic.
Let’s focus on each vulnerability.
“Unquoted service path”
First things first – why would it should even work?
Let’s say we have a service called “MyService” and its path is: C:\Test\My Folder\Test.exe
The default behavior of windows in case the path is unquoted would be trying to run the first exe file which its name matches the first word of one of the folders with a space along the way. If none of the exe files exists, it will run the real exe file.
In our case, the “My Service” would call C:\Test\My.exe (if it exists)! that means, we can exploit this kind of behavior.
For more information, read here.
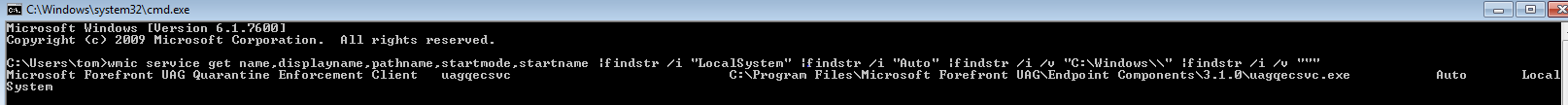
In order to find out which service is automatic, running under system permissions and has no quotes on the process path, we can use wmic.
This command is useful:
wmic service get name,displayname,pathname,startmode,startname |findstr /i “LocalSystem” |findstr /i “Auto” |findstr /i /v “C:\Windows\\” |findstr /i /v “””
Explanation – this command actually requests, using wmic (Windows Management Instrumentation Command-line), to show us all services that matches these conditions (using “findstr” command to filter the results):
- running under “LocalSystem”
- running automaticaly
- the process path is not under c:\windows
- has no quotes (we will see why it is important shortly)
Now, we can see that the path is unquoted and that there is a folder with space in its name (actually, 3 folders). We want to check the permissions on the second folder with “icacls” command:
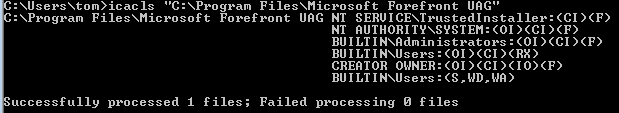
We can see that we had luck on the second folder “Microsoft Forefront UAG” – WD (Write Data) and WA (Write Attributes). Bingo for us!
All we need to do now is to write our own exe file with the name “Endpoint.exe” and place it inside that folder. After a restart, the service will run our exe file automatically with SYSTEM permission, for example – open a reverse shell to remote server, promote local or domain users to local Admins group etc.
“Weak permissions on the exe file”
Same concept here – if we can find a process that runs automatically during startup with system permissions and we can modify that process, the way to system permissions is a short way!
All we need to do is check processes of installed app or service on the machine and check the permissions on the process. If we have permissions, just rename the process and copy a exe with same name to its containing folder. The next startup, your exe will fire up with high privileges, doing whatever you like.
One tool to make our lives easyer would be accesschk.exe or accesschk64.exe by SysInternals. Download here.